
Developing and implementing an effective breach response plan
Breach response planning has been likened to fire preparedness in an office building. Proponents of this thinking argue that cybersecurity should be a non-negotiable component of responsible workplace practices – just like a fire evacuation plan. This is a practical and appropriate way of looking at the issue, with one important consideration: A data breach is actually significantly more likely than a fire.
The Privacy Rights Clearinghouse estimates that more than 900 million records were compromised from 5,000 data breaches since 2005. Alarmingly, these figures only reflect what is currently known and reported. The 2012 breach of LinkedIn (thought to involve 6.5 million users) actually may have involved 117 million users. The stolen email and password combinations were linked to several high-profile social media hacks, including the Twitter account of Mark Zuckerberg. Point being, no one is completely safe.
The best-prepared organizations are shifting their cybersecurity strategies from focusing on outright prevention, to implementing techniques to quickly detect breaches and limit the damage once a breach has been confirmed.
The best solution is to create a robust and replicable incident response plan that allows for preparation and development of a breach response program, detection and analysis, containment/eradication and recovery and post-incident assessment and audit. This section is intended to help organizations understand where to start.
Development of a breach response program
The first step for organizations of all sizes is to develop a response program. This is easier said than done. With a patchwork of inconsistent laws governing required notification and response times across the 50 United States and the federal government, establishing an appropriate protocol or response program can be a complicated endeavor. Breach impact and response affects leaders across an organization – all of whom need to be part of the planning. What’s more, many organizations have business partners who may either be affected by a breach or who could potentially be the site of a breach. This adds an additional layer of regulatory and communication complexity. Preparing the response program is best addressed one step at a time. The team should include IT and data experts, as well as legal, compliance, finance, government affairs and corporate communications.
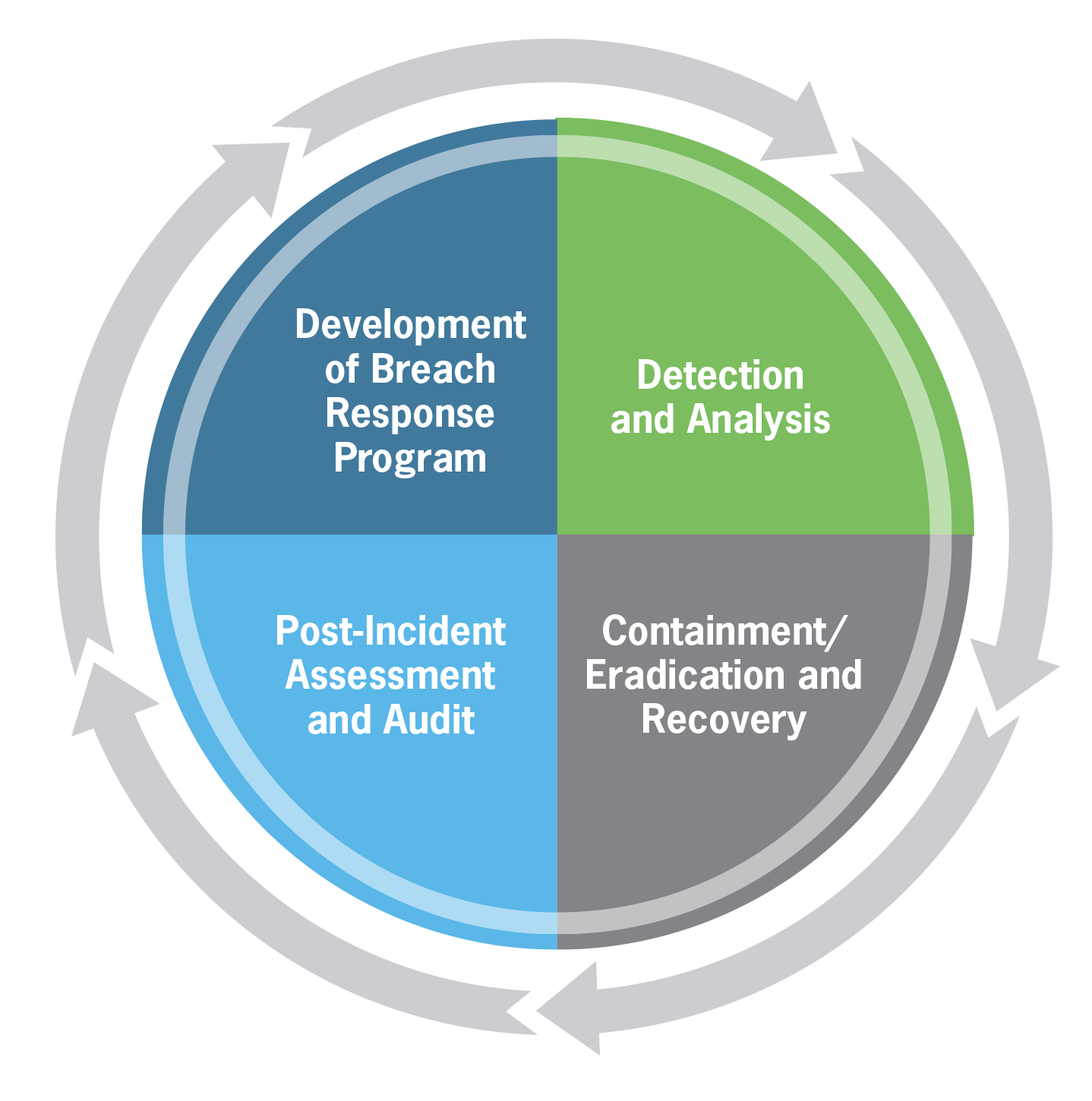
Steps for developing the breach response program include:
- Create an incident response team – If a breach or cyberattack occurs, the impact is felt across functions and the response should be executed accordingly.
- Designate a responsible executive – A responsible executive is the key decision-maker during the breach, who coordinates the response, acts as liaison between management and the response team, coordinates efforts among all groups, notifies appropriate people within the organization and externally, documents the response, identifies key tasks and estimates remediation costs. This is a critical role, so a backup should also be identified.
- Inventory the monitoring tools on your systems – When a breach occurs, it is not uncommon for senior leadership to engage a forensic expert to investigate. The expert may request documentation and logs detailing the breach. These systems and relationships should be in place before a problem arises. A planning process enables an organization to understand where there might be gaps in existing tools.
- Identify the signs of a potential breach – Depending on the tools in place, specific warning signs may exist. For example, one U.S. retailer had a tool in place to identify unusual activity on its systems. Warnings were graded based on likelihood and severity and these notices were communicated to individuals who could act on them.
- Establish a protocol if a breach is suspected – The National Institute of Standards and Technology states that “an essential part of containment is decision-making (e.g., shut down a system, disconnect it from a network, disable certain functions). Such decisions are much easier to make if there are predetermined strategies and procedures for containing the incident.” In other words, it doesn’t make much sense to wait until you’re in the middle of an emergency before you decide how to handle it. The breach protocol will outline the steps to be taken.
- Define reporting / notification process – In certain circumstances, the organization may need to notify law enforcement of the breach. Law enforcement may have procedures that they would like to take to determine the source of the attack and monitor the activity of the attacker. Being able to determine the source of the problem is important because the organization will know how to stop the attack, and will also be able to monitor the attacker’s movements, if needed. In addition, various protocols for notifying affected individuals and the public will need to be outlined.
- Define recovery procedures – These procedures determine how compromised data will be recovered given a variety of hypothetical circumstances (e.g., loss, theft, disaster, etc.). To ensure that data is not completely lost in the event of a hack, organizations should have effective controls and processes in place around data backup and data organization. Organizations should also perform annual restoration testing of this data to ensure that if the data is ever needed, it is being backed-up in a way that can be recovered.
- Test and refine the response plan – In order to prepare for a breach, organizations should train staff on how to react in the event of a breach. Training staff could effectively be completed by simulating a data breach and performing tabletop testing. This allows personnel to practice the steps they need to take in the event of a breach. The first time personnel practice these procedures should not be during a real data breach. These procedures should be practiced early so that personnel can act calmly and efficiently when a breach does occur.
Detection and analysis
When it comes to breach detection and the concurrent ability to be proactive, most companies have a long way to go.
For example, one study found that only 19 percent of breaches in 2014 were self-detected. The remainder was reported by individual victims or law enforcement. The best practice here is to get the right systems, people and processes in place, and then to ensure that tools are being monitored.
With a proper response program in place, all members of the incident response team will be prepared to take action to handle the incident when a breach occurs. This will include several steps:
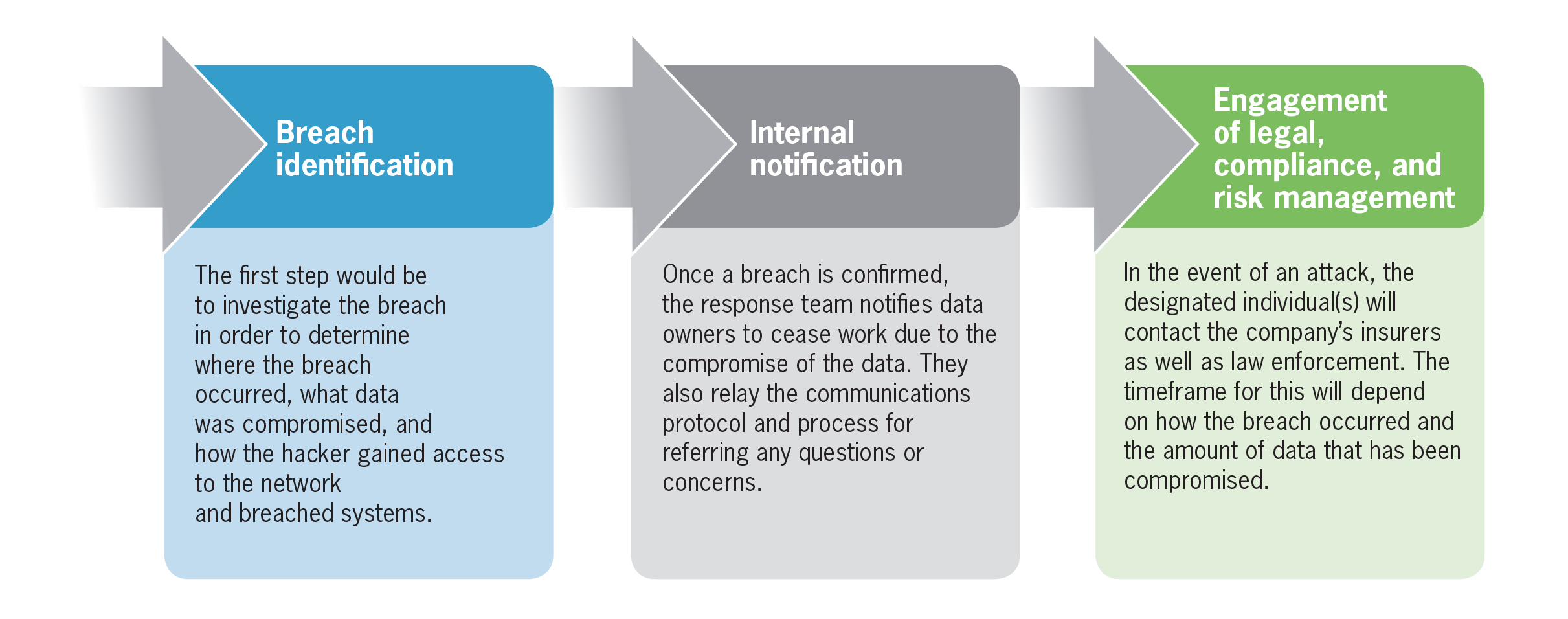
Containment/eradication and recovery
Once a breach or data loss is confirmed, the urgent priority is to stop the bleeding and limit the amount of data that is exposed. This can be more time consuming than organizations might realize. Depending on the circumstances, recovering and repairing the system might be more difficult than anticipated. A few examples:
- Some breaches are slow moving – they may have been in the system for years and are designed to evade detection. Determining the full scope of the impact and rectifying it could take months from the time of discovery.
- Malware could involve relatively easy fixes, or it could be so embedded in the system that repair is a major technological challenge.
- Ransomware – this is when the perpetrator cripples a system until a ransom is paid and depends on the situation. For example, if a single employee laptop is infected, it would be removed from the system and repaired offline. If it is a more pervasive system-wide issue, containment could involve a considerable investment of technological resources.
- Physical theft, loss or damage (such as in a natural disaster) could involve recovery from off-site back-ups with the main focus on external communications.
The response program should account for these possibilities and many others. As a result, all of the key players will know exactly how to respond. This also eliminates the challenges faced by organizations that have not invested in the planning process – chiefly that the first few weeks after discovery may be wasted in finger-pointing and debating what steps to take. This will also be a phase of considerable communication with outside parties, including:
- External notification: External reporting may include customers, business partners and the public at-large. The nature of the breach, the individuals impacted and legal requirements in different jurisdictions will influence what this communication looks like and how it is issued.
- Public relations and communications management: The plan will identify response protocols (e.g., where questions from the press and public are referred) and outline the legal requirements, making this aspect much easier. Because a clear protocol and path forward is in place, spokespeople will be able to speak from a place of transparency rather than spin. This can provide a boost to credibility at exactly the time it is needed most.
- Coordination with law enforcement: This is an area that is often underestimated because people assume that it amounts to reporting that is compliant with regulations. It is important to know, however, that the site of a data breach is often considered a crime scene. Law enforcement may even insist that they take over a system entirely (essentially wrapping the system with yellow police tape). They are rightly concerned about evidence, chains of custody, and the like, but it doesn’t alter the fact that the affected organization has a business to run. Negotiations can be acceptable in this instance and upfront planning for how to ensure law enforcement gets the information they need will help immeasurably. This also underscores the importance of having the right person in the privacy officer role. For example, general counsel might be better equipped to negotiate with law enforcement than someone on the technical side.
The key to maintaining trust and building credibility is a proactive and thoughtfully crafted response plan that prioritizes mitigation and containment, and is executed effectively and rapidly.
Post-incident activity/post-breach assessment and audit
The final step after the breach has been eradicated is to hold a post-breach assessment. Since a data breach occurred, the organization should perform an assessment to determine if other data is at risk. There are third-party services that are able to conduct an information technology risk assessment, network vulnerability assessment, penetration testing and many other types of IT assessments to determine if there is a weakness that could be targeted. This risk assessment may allow the organization the opportunity to identify and even avoid other potential data breaches into the system.
An audit of the incident response program can help to ensure the continued relevance of the plan. Systems, technology and threats change, so the plan should be reviewed at least once a year. This ensures that the plan contains accurate and current information, allows the breach response process to be assessed and fine-tuned, identifies new potential issues and establishes accountability for the overall plan. Organizations where there is no internal audit function in place should be sure to have the incident response team review the plan once a year to keep information fresh.
Next steps - Developing and implementing an effective breach response plan
The way forward is to recognize that all data is at risk, and to prepare and plan for all possible scenarios. The key to maintaining trust and building credibility is a proactive and thoughtfully crafted response plan that prioritizes mitigation and containment, and is executed effectively and rapidly. Stakeholders will thank you for it.
For more information on this topic, or to learn how Baker Tilly specialists can help, contact our team.
