
Monitoring and verifying cybersecurity controls effectiveness
A critical requirement for any cybersecurity management program is verifying the effectiveness of established controls. While most leading cybersecurity control frameworks include verification controls, we call special attention to this as part of the process of managing cybersecurity. Periodically, organizations should evaluate their security controls to determine whether the cybersecurity controls are operating as intended.
There are three primary ways to implement processes to monitor cybersecurity control performance and effectiveness:
- Establish and regularly review security metrics
- Conduct vulnerability assessments and penetration testing to validate security configuration
- Complete an internal audit (or other objective assessment) to evaluate security control operation
Establish security metrics
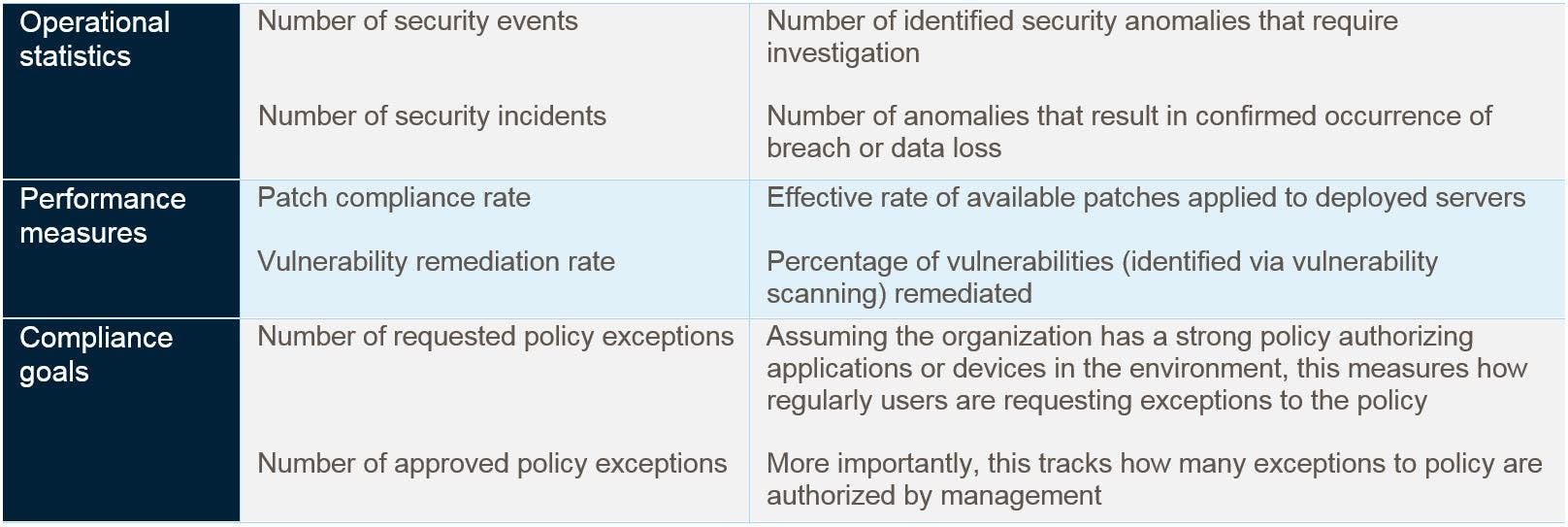
When it comes to process management, it’s often stated: “You can’t manage what you can’t measure.” It’s no different with cybersecurity. By defining the specific objectives of your security program, you can develop specific measures and monitor these measures over time to gauge process performance. You can think of security performance measures in three main categories (see figure below):
- Operational statistics include the counts of activity within an environment. These don’t necessarily reflect action by the organization, but they do help to build a general awareness of security-related activity within an organization.
- Performance measures are derived or calculated metrics that quantify an organization’s behavior or performance against a stated objective. We think of these in terms of specific action taken by employees to help maintain an organization’s security posture.
- Compliance goals are a specific type of performance measure focused on demonstrating whether an organization is complying with organizational policy.
Conduct vulnerability assessments and penetration testing
In order to verify the effectiveness of security configuration, all organizations should conduct vulnerability assessments and penetration testing. The purpose of the vulnerability assessment is to identify system security patches the organization may have missed or any weak security configurations the organization has applied. Security firms use a variety of automated scanning tools to compare system configurations to published lists of known vulnerabilities.
Penetration testing takes vulnerability scanning a step further. A skilled, ethical hacker leverages identified vulnerabilities and simulates real-life attack scenarios to determine whether these vulnerabilities can be exploited and lead to an actual breach. An organization can use the results of vulnerability scanning and penetration testing to identify any security gaps as well as consider the root cause of what permitted these vulnerabilities to get introduced within the organization.
Given the current state of information security and the constant evolution of security threats, it is imperative that internal audit departments act as a third line of defense and verify cybersecurity control performance to assist in enhancing the overall security posture of the organization.
Complete an internal audit
We often see organizations with internal audit departments focused extensively on internal controls over financial reporting.
Given the current state of information security and the constant evolution of security threats, it is imperative that internal audit departments act as a third line of defense and verify cybersecurity control performance to assist in enhancing the overall security posture of the organization.
Leveraging the results of a cybersecurity risk assessment, a good verification process begins with the review of organizational cybersecurity policies, procedures, guides and standards. A successful cybersecurity internal audit needs sponsorship from executive management to facilitate the process. Internal audit kicks off the audit process by conducting interviews with key stakeholders to confirm an understanding of the activities taking place with respect to satisfying cybersecurity control objectives.
As part of the audit, it would be typical to conduct a gap analysis against either the organization’s security policy and standards, or an independent control framework (reference previous section) to determine whether cybersecurity controls are suitably designed to meet the security objective, and that they are in place and aligned with the organization’s risk assessment. Additionally, it’s important to evaluate whether personnel roles and responsibilities for cybersecurity are clearly defined and properly assigned to employees with sufficient skill and authority to perform these controls.
Based on the results of the design evaluation, an organization can provide higher levels of assurance by determining whether cybersecurity controls are operating effectively. The audit team will use the organization’s documented security policies and procedures to establish cybersecurity control audit testing procedures. Evidence of control activity performance is then obtained and reviewed for all controls that have a manual component, e.g., user account management, infrastructure and application change management, and systems backup. Lastly, for systems based controls, e.g., firewall settings, antivirus settings, data encryption settings, internal audit examines specific systems configurations to determine whether they are set as expected.
In the absence of an in-house internal audit capability to address cybersecurity risks, consider leveraging an objective third party to undertake a similar assessment.
Next steps - Monitoring and verifying your cybersecurity controls
The current state of cybersecurity and rapidly evolving threat landscape mean that cybersecurity is not a one- time event. Once controls have been implemented, an organization needs to monitor its control environment to confirm that controls remain effective. By combining security metrics, internal audit control testing and regular vulnerability/penetration testing, an organization can help to ensure that its cybersecurity program remains effective and evolves appropriately with the organization.
For more information on this topic, or to learn how Baker Tilly specialist can help, contact our team.
