
U.S. cybersecurity executive order could mean changes for many organizations
On February 12, 2013, President Obama signed the highly anticipated executive order on cybersecurity. The order focuses on the growing concern of cyber intrusions on the nation’s critical infrastructure. To combat this issue the US Government is looking to:
- Form partnerships with private sector businesses that maintain critical cyber assets
- Share cyber threat information between the government and private sector
- Collaborate on the design and implementation of risk-based standards
While the specific details of how this order affects private sector entities is still to be determined, here is a summary of the order’s main components:
Critical infrastructure
The President defines the term critical infrastructure to mean, "systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters."
Collaboration with private sector
Not only does this order seek to disseminate cyber threat information from the government to private sector entities, but also to obtain information from the private sector businesses who volunteer to participate. The Department of Homeland Security (DHS) will be working with the private sector to develop incentives for the private sector entities to participate in the program. Also, the Critical Infrastructure Partnership Advisory Council will work with critical infrastructure owners, sector-specific agencies, independent regulatory agencies, and other relevant agencies to coordinate improvements while the National Institute of Standards and Technology (NIST) will be responsible for developing a cybersecurity framework.
Cybersecurity framework
As a foundational framework the Secretary of Commerce will direct NIST to lead in the development of a set of standards, methodologies, procedures, and processes that align governmental policy, business, and technological approaches to address cyber risks. The framework is aimed at being technology-neutral as to address security gaps in computer networks and systems for critical infrastructure, such as the electric grid, water plants, transportation networks, and financial networks.
Eligibility requirements
Participation in the program is voluntary, but the entity must be identified as an eligible candidate to participate. The Secretary of Homeland Security will use a "risk-based approach to identify critical infrastructure where a cybersecurity incident could reasonably result in catastrophic regional or national effects on public health or safety, economic security, or national security." Eligibility will be determined with the help of sector-specific and other relevant agencies to provide the Secretary with the information needed to identify agencies that maintain or offer commercial security services to critical infrastructure.
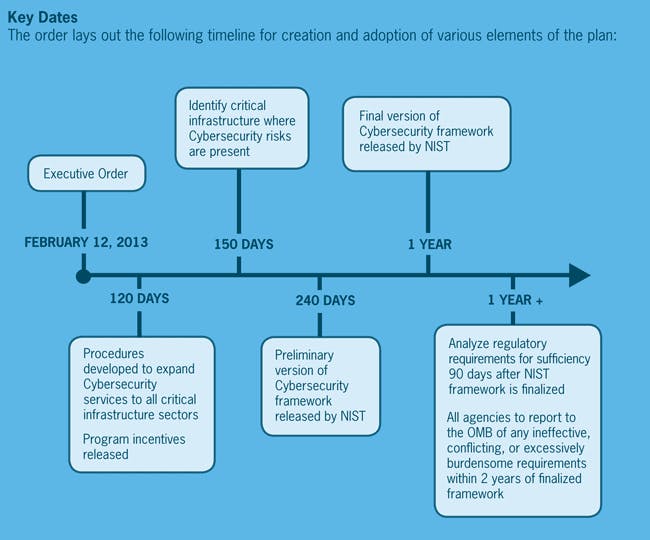
US cybersecurity executive order timeline