Cybersecurity Maturity Model Certification (CMMC) raises the bar for contractors
The United States Department of Defense (DoD) will require organizations conducting business with the DoD (i.e., defense contractors) to obtain a Cybersecurity Maturity Model Certification (CMMC) involving verification from an independent assessor. This is expected to have an impact across the Defense Industrial Base (DIB). What can contractors do now to prepare their organizations to meet these new requirements?
Depending upon the CMMC maturity level required, implementation and certification of cybersecurity controls may require a time-consuming commitment of resources, both in terms of people and funding. This heightens the urgency for acting now rather than waiting. Consider addressing your CMMC challenges in a pragmatic way by leveraging Baker Tilly’s relevant expertise.
Introduction
The rollout of CMMC is a major development in the cybersecurity regulatory landscape and will have significant impacts on defense contractors of all sizes. With the release of this model, in order to conduct business with the DoD, essentially all defense contractors will be required to achieve a defined CMMC level(1) involving a certification to be conducted by an independent and qualified third-party assessor.
Not only will the DoD require defense contractors to comply with these new requirements, but also to flow-down these requirements across their supply chains, adding further subcontract oversight and risk burdens to higher-tier contractors.
CMMC overview and background
The DoD intends to use the CMMC to manage cybersecurity risk across the DIB – specifically with respect to protecting federal contract information (FCI) and controlled unclassified information (CUI) – through independent certification to verify defense contractors’ cybersecurity posture. Results of these certifications will become discriminators within the DoD’s solicitation and award processes.
In addition, the DoD aims for the CMMC to expand and improve upon existing guidance for adequate cybersecurity controls, aligning cybersecurity safeguarding requirements with contractors’ risk exposure when handling FCI and CUI in performance of DoD contracts.
The CMMC does not replace current regulations and standards, such as DFARS 252.204-7012, “Safeguarding Covered Defense Information and Cyber Incident Reporting,” and NIST SP 800-171, “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.” Rather, it builds upon existing guidance by introducing additional standards that transition away from the current self-reporting approach, to a new paradigm involving an independent verification process with defined risk considerations based on scope and requirements of specific DoD contracts.
Key elements of CMMC requirements
The CMMC currently includes the following key elements:
- Essentially, all organizations conducting business with the DoD(2), whether as a prime or subcontractor, will need to achieve, at minimum, a “level 1” maturity certification.
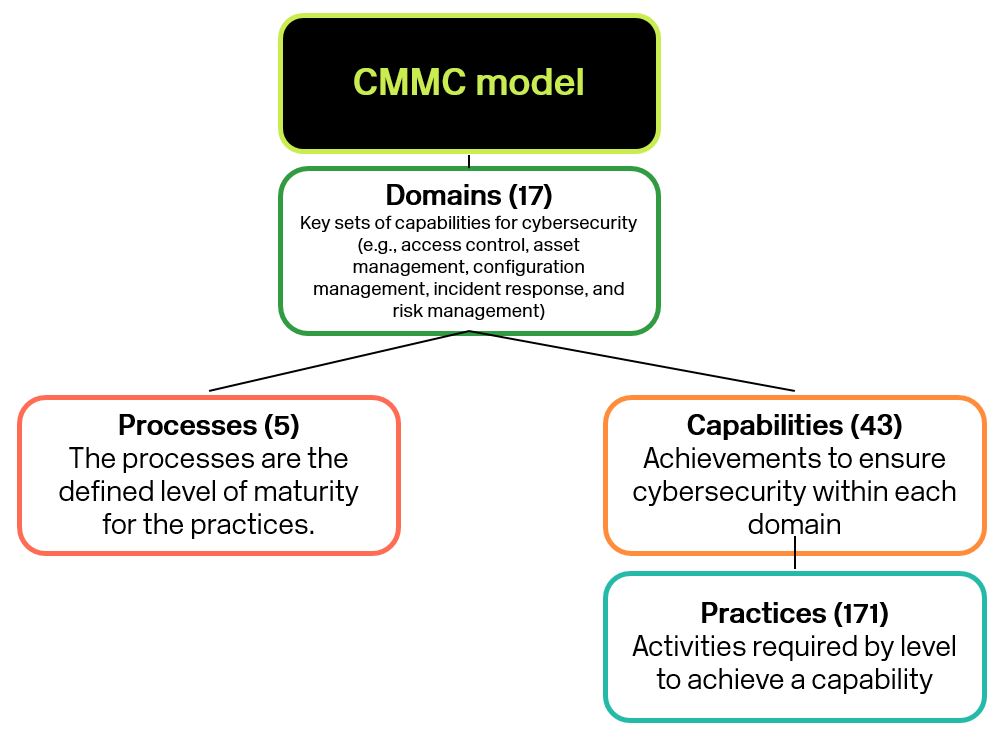
- The model organizes the required cybersecurity safeguards into a set of domains, with subsequent capabilities and processes (see graphic below).
- The model maps the required domains to maturity levels ranging from “level 1” (basic cyber hygiene) to “level 5” (advanced/progressive), where each level contains specific capabilities and practices necessary to mitigate increasing degrees of cybersecurity risk.
- In order to achieve a specific maturity level, the organization must also achieve all preceding level(s) (e.g., to achieve “level 3” maturity, you must first achieve both “level 1” and “level 2”).
- The DoD will require organizations to engage a certified third-party assessor organization (C3PAO) to assess the level of maturity achieved.
- In general, CMMC certificates are expected to be valid for three years(3).
- The DoD will not publicize the certification levels achieved by defense contractors; the DoD will have access to all DIB companies’ certification levels.
- The DoD envisions an affordable and cost-effective certification process, and has publically confirmed the allowability of costs reasonably incurred to achieve certification.
- The CMMC Accreditation Body has been created to manage, operate, and sustain the certification program that will include the training, evaluation, and accrediting of C3PAOs.
- The DoD plans to include CMMC requirements within some requests for information (RFI) and requests for quote / proposal (RFQ / RFP) by June and Fall 2020.
What should contractors do now to prepare for CMMC?
Baker Tilly recommends that contractors follow a three-phased approach to prepare their organization to meet their desired maturity level prior to the certification. The approach is outlined below:
- Readiness
-Inventory all existing DoD contracts, subcontracts, awards and agreements.
-Inventory all systems that collect, store, and process FCI and CUI.
-Conduct a gap assessment of current cybersecurity controls relative to the model and determine remediation activities to achieve desired certification level. - Remediation
-Prioritize remediation activities.
-Implement remediation activities.
-Reassess cybersecurity controls. - Documentation
-Document cybersecurity policies and desired certification level.
-Formalize relevant controls in procedural documentation.
-Assemble all documentation in preparation for certification.
In addition, defense contractors should assess their supply chain management (SCM) capabilities to identify where they need to strengthen processes and controls around flowing down, monitoring and managing cybersecurity safeguarding requirements relative to DFARS 252.204-7012, NIST SP 800-171, and the Defense Contract Management Agency’s Contractor Purchasing System Review (CPSR) Guidebook.
By following Baker Tilly’s methodology, defense contractors can proactively identify any deficiencies and begin corrective actions to meet their desired CMMC level. Early action in this regard will reduce the risk of being precluded from DoD business opportunities while preparing to become certified. Baker Tilly stands ready to help organizations to proactively complete these steps and position their organizations to meet their desired certification level.
For more information on this topic, or to learn how Baker Tilly specialists can help, contact our team.
1. Organizations that solely produce Commercial-Off-The-Shelf (COTS) products do not require a certification, FAQ 19)
2. Organizations that solely produce Commercial-Off-The-Shelf (COTS) products do not require a certification, FAQ 19)
3. Organizations that solely produce Commercial-Off-The-Shelf (COTS) products do not require a certification, FAQ 15)