CMMC 2.0 FAQ

What is the availability of getting an assessment?
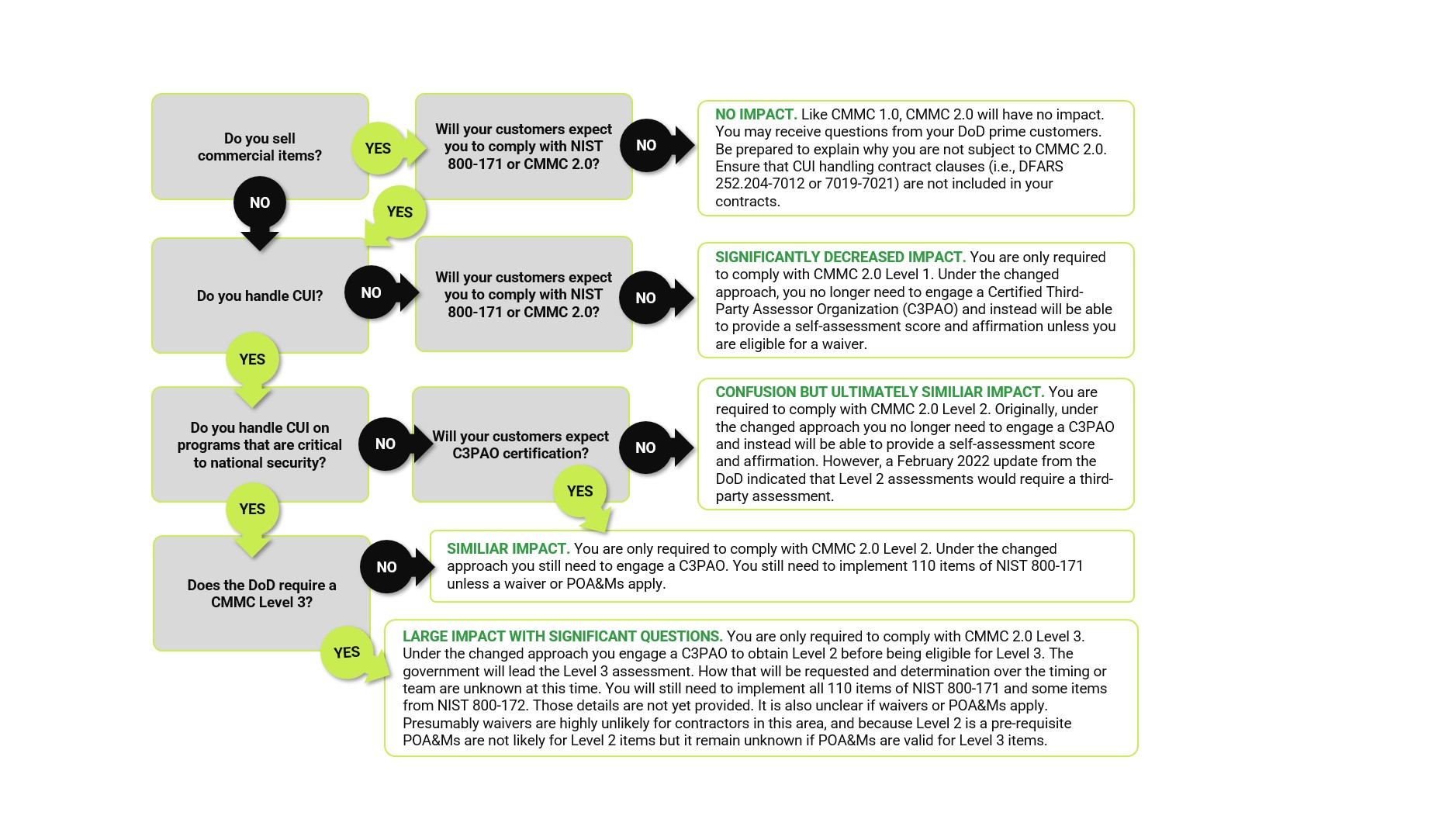
In CMMC 2.0 at Level 2, to complete an independent assessment, you will need to leverage a C3PAO. This is a free-market option and, assuming availability, it should be easy to engage a C3PAO. If you require Level 3,a government-led assessment, the request process and the amount of lead time required is not yet known.
Who is eligible for a Level 2 self- assessment?
The DoD indicated that “a subset of programs with Level 2 (“Advanced”) requirements do not involve information critical to national security, and associated contractors will only be required to conduct self-assessments.” How many programs do not involve information critical to national security? If that is a low percentage then it would be fewer companies that can use a self-assessment for Level 2. Who will make that determination? If the contracting officer is the one to make that call, do they error on the side of caution? Does making that call require more or less work for the contracting officer? Can the contracting officer decide that the prime is handling information critical to nation security but the subcontractor is not? How this will work is critical and not yet explained.
What are the requirements in the contract tied to the Program or data?
Under CMMC 1.0, it was not clear if the contract would say that CMMC Level X is required if you are on this program or if you are on the program and possess CUI. In the later case, it would allow a subcontractor who doesn’t obtain CUI to still perform on the contract with a lower level requirement. The DoD stated, “a subset of programs with Level 2 (“Advanced”) requirements do not involve information critical to national security, and associated contractors will only be required to conduct self-assessments.” So it seems they intend to allow this, but exactly how this will occur is not yet clear. Will contractors be able to decide? Will the DoD be explicit in rulemaking or the contracts?
Where will level requirements be spelled out? In the contract, tied to the program or based on the data?
CMMC will be required when a contractor is handling CUI. However, the level should be spelled out in the contract. If a contract is not handling CUI, it will likely require Level 1. It is expected that under CMMC 2.0, the contract would say that CMMC Level X is required if you are on this program or if you are on the program and possess CUI. In the latter case, it would allow a subcontractor who doesn’t obtain CUI to still perform on the contract with a lower-level requirement. The DOD stated, “a subset of programs with Level 2 (“Advanced”) requirements do not involve information critical to national security, and associated contractors will only be required to conduct self-assessments.” So, it seems the DOD intends to allow this, but exactly how it will occur is not yet clear. Will contractors be able to decide? Will the DOD be explicit in rulemaking or the contracts?
If I have a third-party assessment, will I still need to self-assess?
It is not clear at this time, however, the DOD said it is considering asking for contractors to annually confirm even when they have certification. Because the CMMC certification is good for three years, it makes sense that the DOD would want to have a confirmation from the contractor that its environment is still in compliance with the requirements.
When will waivers be allowed?
The DOD said waivers will be “allowed on a very limited basis in select mission critical instances, upon senior leadership approval.” This statement reveals that it is not a frequent occurrence. Who receives the waivers – and how – is still to be determined. The DOD’s comments since CMMC 2.0 was released further confirmed waivers would be limited in nature. It also implied waivers would be sought by the DOD before the contract is executed or even the solicitation occurs.
What are the restrictions for POA&Ms?
The DOD denoted that “highest weighted requirements cannot be on POA&M list” and “DoD will establish a minimum score requirement to support certification with POA&Ms.” This means that the practices from NIST 800-171 that carry three- and five-point values in the DOD assessment methodology are likely not eligible for POA&M. Additionally, organizations would need to achieve a minimum score before becoming eligible for POA&Ms. Where that score is set is not known. The POA&Ms are also only an option for a limited time. It is sounding like the DOD is planning for that to be less than six months, which means a POA&M will not be eligible for most of the controls and, if used, is only good for a limited period.