
Securing a new foundation for supply chain security: CISA task force releases year two report
On Dec. 17, 2020, the Cybersecurity and Infrastructure Security Agency (CISA), in close collaboration with its Information and Communications Technology (ICT) Supply Chain Risk Management (SCRM) Task Force[1] published its “Year 2 Report” evaluating the current ICT supply chain landscape and provided recommendations to help companies and government agencies enhance their SCRM capabilities. Established in December 2018, the ICT SCRM task force is made up of representatives from 20 federal agencies and 40 industry organizations across the IT and communications sectors.
The “Year 2 Report” builds on findings from year one and is likely to be increasingly significant going forward, in light of the impact of COVID-19 on the resiliency of global supply chains and the recent SolarWinds supply chain infiltration. Specifically, the report presents and summarizes the findings of five working groups that endeavored to target interrelated supply chain and cybersecurity problems. The task force has been re-chartered for 2021 and will work on operationalizing their recommendations. The working groups explored issues including:
- Legal challenges to information sharing between supply chain members
- Threat evaluation
- Qualified bidder lists/qualified manufacturer lists (QBL/QML)
- Vendor SCRM
- Supply chain challenges related to the COVID-19 pandemic
Working group summary and highlights
A brief overview of the activities, conclusions and recommendations of the working groups, as outlined in the year two report, is provided below:
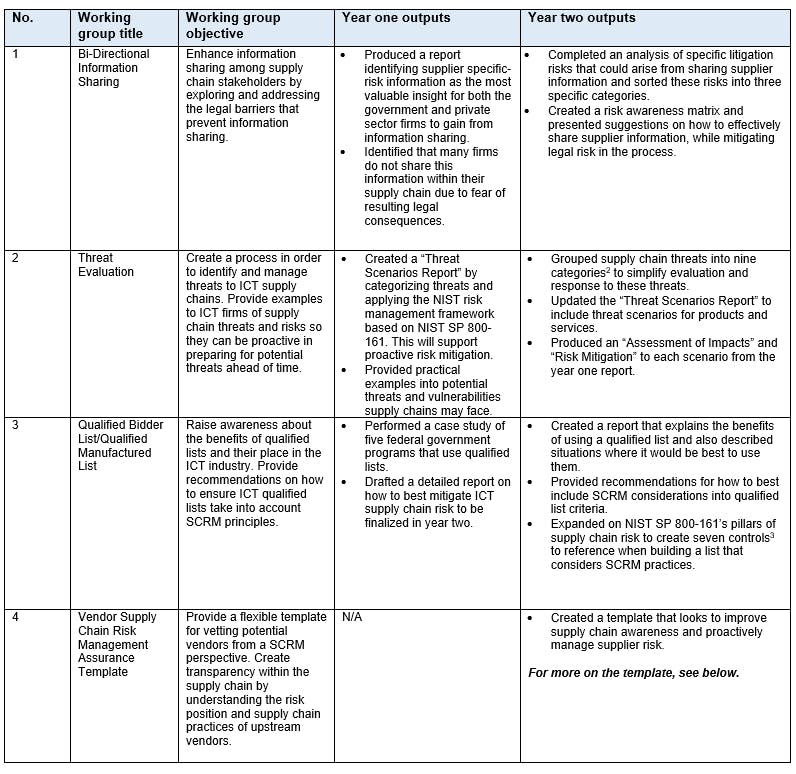
In focus: benefits of the working group No. 4, Vendor SCRM Assurance Template
The outputs of working group No. 4 are of particular interest to federal contractors. Working group No. 4 effectively pulls together many of the key points from other working groups to create a flexible template that can be used to assess SCRM management practices and ICT suppliers’ supply chain assurance efforts, and to potentially identify risks ahead of time. The Vendor SCRM Assurance Template was constructed to provide an actionable guide which contractors (both large and small) can use to gain more insight into SCRM compliance and the behavior of their suppliers. It also leverages “existing tools and resources, including NIST SP 800-161 and ISO standards.” Contractors should consider how this tool could benefit their own SCRM practices going forward. The task force has stated that the template will be approved soon and posted on the CISA website for public consumption.
Conclusion
ICT supply chains are complex, dynamic ecosystems representing a critical threat vector – one that requires focused attention and investment. As noted above, the ICT SCRM task force’s “Year 2 Report” provides helpful guidance and valuable resources for federal agencies and private entities that can be used to identify, prepare for and respond to supply chain threats. Contractors should strongly consider employing the report’s findings and materials to bolster the resilience and security of their supply chains. As always, Baker Tilly stands ready to help federal contractors address their supply chain risk management needs as they arise.
For more information on this and SCRM, or to learn how Baker Tilly specialists can help – please contact us.
[1]The ICT Supply Chain Risk Management (SCRM) Task Force – sponsored by CISA’s National Risk Management Center (NRMC) – is the United States’ preeminent public-private supply chain risk management partnership, entrusted with the critical mission of identifying and developing consensus strategies that enhance ICT supply chain security. More information on the task force is available at:https://www.cisa.gov/ict-scrm-task-force. Note, the ICT SCRM Task Force is a partnership between the IT Sector Coordinating Council (https://www.it-scc.org/) and the Communications Sector Coordinating Council (https://www.comms-scc.org/).
[2]The nine categories of supply chain threats noted by working group No. 2 include: Counterfeit Parts, Cybersecurity, Internal Security Operations and Controls, System Life Cycle Processes and Tools, Insider Threats, Economic Risks, Inherited Risks, Legal Risks, and External End-to-End Supply Chain Risks.
[3]The seven controls listed by working group No. 3 include Physical Security, Cyber Security, Personnel Security, Hardware Integrity, Software Integrity, Supply Chain Resilience, and Supply Chain Quality.

