
Take a proactive security approach to your containerized applications
With Gartner estimating that by 2026, 90% of global organizations will be running containerized applications in production[1], containerized applications are quickly surpassing traditional software development and deployment as the core component of today’s dynamic technological framework. However, as containers become more widely used, security concerns continue to increase. To guarantee the confidentiality, integrity and availability of applications, these security vulnerabilities must be proactively addressed and remedied.
Containerized applications and their security concerns
Containerized applications are software programs and their dependencies packaged together in a self-contained environment called a container, which ensures consistent and efficient deployment across different cloud computing environments and represents a progressive step in the evolution of provisioning IT services. Containers can be thought of as a miniature computer that functions like a self-contained unit, housing both the operating system and all the accompanying code, neatly packaged for deployment.
Problems arise when organizations overlook security to eagerly adopt containers under the mistaken belief that they are inherently secure and impervious to vulnerabilities. With their constant changes and dependencies, containers' dynamic nature presents a special vulnerability and management difficulty. Traditional security tools are not thorough or flexible enough to adequately identify vulnerabilities and with the rate of change in container environments being too rapid for manual scanning and retroactive patching, there is a pressing need to put strong security controls in place.
The solution: Inline scanner integration
An inline scanner is a type of security tool that is integrated directly into a network to continuously monitor, inspect and analyze the data passing through it in real-time to mitigate security threats such as malware, viruses or malicious activities. This real-time monitoring and immediate response capability make inline scanners an essential component of network security infrastructure, helping organizations protect their systems and data from various cyber threats.
When integrated into a containerized application, inline scanners offer a means to deploy containers on an enterprise level by proactively addressing the need for security controls. Instead of the traditional process of uploading, running scans and discovering vulnerabilities later, an integrated inline scanner takes a proactive approach in the development cycle by conducting proactive virus scanning and vulnerability assessments on containers prior to deployment.
Additionally, this approach allows your organization to regularly update your code, re-scan container images and ensure that the container’s underlying operating system is up to date, serving as a substantial risk mitigation strategy in helping to prevent vulnerabilities.
Real world application: Lacework inline scanner with AWS CodeBuild and AWS CodePipeline
As Baker Tilly Digital actively works to adopt a container-first strategy for application development, we have developed a way to smoothly integrate the Lacework Inline Scanner[2] with AWS CodeBuild and AWS CodePipeline into our continuous integration and continuous deployment (CI/CD) pipeline to actively scan containers for vulnerabilities to strengthen the security posture of our company.
This process begins with the developer making changes to the repository in GitHub which triggers the build process in AWS CodeBuild. Then, the container image is built, scanned for cyber threats and securely pushed to the container registry.
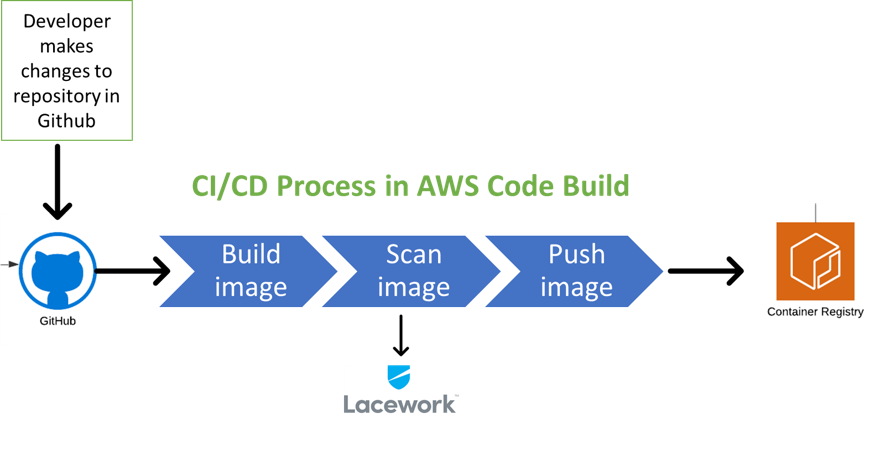
Our dedication to creating secure and dependable software is strengthened by the ability to identify and address container issues early in the development process and our containerized apps are protected against potential threats from the outset thanks to the scanner’s automatic and real-time vulnerability evaluation.
Key features and benefits include:
- Continuous vulnerability scanning: The CI/CD pipeline's post-build phase includes an automatic scan of container images by the scanner, allowing our development teams to identify any vulnerabilities in the container images in real-time and address problems at the very beginning of development.
- Early detection and remediation: Address security issues before they enter production systems by identifying vulnerabilities during the development process. This proactive approach drastically cuts down on the time and effort needed to fix vulnerabilities, as well as the danger of possible breaches.
- Comprehensive vulnerability insights: In-depth vulnerability reports are provided by the scanner, which additionally points up potential flaws in the container's supporting layers, packages and dependencies in addition to known common vulnerabilities and exposures (CVEs). We can better comprehend our container security landscape and improve our overall security posture with the support of this degree of visibility.
- Integration with existing CI/CD workflow: Our development workflows are not interrupted thanks to the smooth integration into our current AWS CodeBuild and AWS CodePipeline procedures. Our teams can concentrate on developing secure applications because the scanner's simplicity prevents them from complicating their development procedures.
- Compliance and audit support: We are better able to meet regulatory standards and can convince auditors and stakeholders of our dedication to security by providing them with thorough documentation and a verifiable history of vulnerabilities.
Using the Lacework Inline Scanner combined with AWS CodeBuild and AWS CodePipeline, our organization's proactive approach to container vulnerability scanning is a huge step toward assuring the security and integrity of our containerized apps. Early vulnerability detection and patching helps us strengthen our applications' defenses against threats, lower security risks and improve our overall security posture.
How we can help
Containerized applications are the future of provisioning IT services as they quickly become the core component of today’s dynamic technological framework. But adopting containers without first addressing security concerns opens your organization up to various cyber threats and increases risk.
Though our tested process of integrating Lacework Inline Scanner with AWS CodeBuild and AWS CodePipeline, Baker Tilly Digital can help your organization unlock the full potential of your containerized applications. Interested in learning more about how your organization can take a proactive security approach to your containerized applications? Contact one of our professionals today.
Sources
[1] August 2021, “The Innovation Leader’s Guide to Navigating the Cloud-Native Container Ecosystem,” Gartner
[2] Integrate Inline Scanner, Lacework
